Cybersecurity And Information Assurance
Cybersecurity and Information Assurance: Protecting Digital Assets
In today's digital age, where technology permeates every aspect of our lives, the importance of cybersecurity and information assurance cannot be overstated. As we increasingly rely on technology for personal and professional activities, the need to safeguard our digital assets and sensitive information becomes paramount.
This comprehensive guide aims to delve into the world of cybersecurity and information assurance, exploring the various aspects that contribute to a robust digital defense strategy. From understanding the fundamental concepts to implementing practical measures, we will navigate the intricate landscape of cybersecurity to empower individuals and organizations alike.
Understanding the Basics

Cybersecurity, often referred to as information technology security, encompasses the practices and technologies designed to protect computers, networks, programs, and data from unauthorized access, misuse, and destruction. It involves a range of measures aimed at securing digital assets and ensuring the confidentiality, integrity, and availability of information.
Information assurance, on the other hand, focuses on managing risks related to information and maintaining its accuracy, reliability, and integrity. It ensures that information is protected throughout its lifecycle, from creation to disposal, and is accessible only to authorized individuals.
The Importance of Cybersecurity and Information Assurance

The significance of cybersecurity and information assurance cannot be understated in today's interconnected world. Here's why they are essential:
- Protection against Cyber Threats: With the rise of sophisticated cyberattacks, ranging from malware and ransomware to phishing and social engineering, robust cybersecurity measures are crucial to safeguard against these threats.
- Data Privacy and Security: In an era where data is a valuable asset, ensuring the privacy and security of personal and sensitive information is of utmost importance. Cybersecurity and information assurance practices help prevent data breaches and unauthorized access.
- Business Continuity: For organizations, implementing effective cybersecurity measures is vital for business continuity. A single cyberattack can disrupt operations, lead to financial losses, and damage reputation.
- Compliance and Legal Requirements: Many industries have specific regulations and standards related to data protection and privacy. Cybersecurity and information assurance practices help organizations meet these compliance requirements.
- Trust and Reputation: Demonstrating a commitment to cybersecurity and information assurance enhances an organization's reputation and builds trust with customers, partners, and stakeholders.
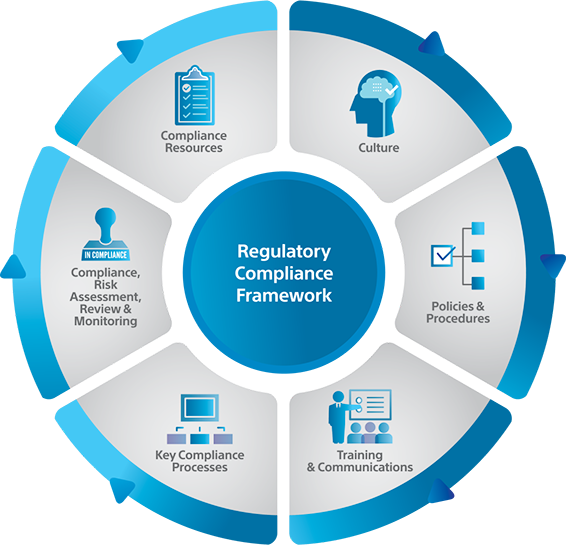
Key Components of Cybersecurity and Information Assurance

A comprehensive cybersecurity and information assurance strategy encompasses various components, each playing a crucial role in safeguarding digital assets. These components include:
Network Security
Network security involves protecting computer networks from unauthorized access, misuse, and disruption. It includes measures such as firewalls, intrusion detection systems, and virtual private networks (VPNs) to secure network traffic and prevent unauthorized access.
Endpoint Security
Endpoint security focuses on protecting individual devices, such as computers, laptops, and mobile devices, from cyber threats. This includes implementing antivirus software, encrypting data, and ensuring regular software updates to patch vulnerabilities.
Application Security
Application security aims to protect software applications from vulnerabilities and exploits. It involves secure coding practices, regular security audits, and prompt patching of known vulnerabilities to prevent unauthorized access and data breaches.
Identity and Access Management (IAM)
IAM is crucial for controlling access to resources and ensuring that only authorized individuals can access sensitive information. It involves implementing strong authentication mechanisms, such as multi-factor authentication, and managing user permissions effectively.
Data Security
Data security focuses on protecting data at rest and in transit. This includes encryption, data loss prevention measures, and secure data storage practices to ensure that data remains confidential and is not compromised.
Disaster Recovery and Business Continuity
Planning for potential disruptions, such as cyberattacks or natural disasters, is essential. Disaster recovery and business continuity strategies ensure that organizations can quickly recover from incidents and resume operations with minimal downtime.
Implementing Effective Cybersecurity Measures

Implementing a robust cybersecurity strategy requires a holistic approach that addresses various aspects of digital security. Here are some key steps to consider:
Risk Assessment and Management
Conducting a thorough risk assessment is the first step in identifying potential vulnerabilities and threats. This involves identifying assets, assessing potential risks, and developing strategies to mitigate or manage these risks effectively.
Security Policies and Procedures
Establishing clear security policies and procedures ensures that all stakeholders understand their roles and responsibilities in maintaining cybersecurity. These policies should cover areas such as password management, data handling, and incident response.
Employee Training and Awareness
Human error is often a significant factor in cybersecurity incidents. Providing regular training and awareness programs helps employees recognize potential threats, such as phishing attempts, and adopt secure practices.
Secure Software Development
Implementing secure coding practices and conducting regular security audits during the software development lifecycle helps identify and address vulnerabilities early on. This reduces the risk of exploitation and ensures the overall security of applications.
Incident Response Planning
Developing a comprehensive incident response plan is crucial for effectively managing cybersecurity incidents. This plan should outline the steps to be taken in the event of a breach, including containment, eradication, and recovery procedures.
Regular Security Audits and Penetration Testing
Conducting regular security audits and penetration testing helps identify vulnerabilities and weaknesses in the system. These tests simulate real-world attacks to evaluate the effectiveness of security measures and identify areas for improvement.
The Role of Artificial Intelligence and Machine Learning

Artificial Intelligence (AI) and Machine Learning (ML) are transforming the cybersecurity landscape by enabling more efficient and effective threat detection and response. Here's how they are making an impact:
Threat Detection and Prediction
AI and ML algorithms can analyze vast amounts of data to detect patterns and anomalies, helping identify potential threats and predict future attacks. This enables organizations to stay one step ahead of cybercriminals.
Automated Incident Response
AI-powered systems can automate certain aspects of incident response, such as threat identification, containment, and mitigation. This reduces the time taken to respond to incidents and minimizes the impact of attacks.
Behavioral Analysis
By analyzing user and system behavior, AI and ML can identify deviations from normal patterns, indicating potential security breaches or insider threats. This behavioral analysis enhances the overall security posture.
Conclusion: Empowering Digital Defense

In an era where cyber threats are ever-evolving, the importance of cybersecurity and information assurance cannot be overstated. By understanding the fundamentals, implementing robust security measures, and leveraging the power of AI and ML, individuals and organizations can fortify their digital defenses and protect their valuable assets. With a comprehensive cybersecurity strategy in place, we can navigate the digital landscape with confidence and ensure the integrity and security of our digital world.
What are some common cybersecurity threats?
+Common cybersecurity threats include malware, ransomware, phishing attacks, social engineering, and distributed denial of service (DDoS) attacks.
How can I protect my personal information online?
+To protect your personal information online, use strong passwords, enable two-factor authentication, be cautious of phishing attempts, and regularly update your software and devices.
What is the role of encryption in cybersecurity?
+Encryption plays a vital role in cybersecurity by protecting data from unauthorized access. It transforms data into an unreadable format, ensuring that even if it is intercepted, it remains secure.
How often should I update my security software and operating system?
+It is recommended to update your security software and operating system regularly, preferably as soon as updates become available. These updates often include security patches that address known vulnerabilities.
What is the importance of backup and disaster recovery planning?
+Backup and disaster recovery planning are crucial to ensure business continuity in the event of a cyberattack or system failure. Regular backups and well-defined recovery procedures enable organizations to quickly restore operations and minimize downtime.
